How to turn off the built-in password manager in Chrome
If you often use the same websites, you’ll notice Chrome asks whether…
How to Stop Programs from Loading at Startup
If Windows takes a long time to start, maybe there’s too much…
How to Accurately Predict Annual Hardware Expenses
Pulling together your budgets for next year? While it might be hard…
The Top Benefits of Multi-Factor Authentication
If your organization is prioritizing cybersecurity, multi-factor authentication (MFA) is a must-have…
Do you know how easy it is for your business to be hacked?
Watch as a certified ethical hacker breaks into 3 computers in just…
Would you or your employees click on a phishing link?
Criminals send emails pretending to be someone they’re not, hoping one of…
Are you looking for a technology partner?
With our clients we work on all aspects of their technology, especially…
How to protect your webcam from spies.
A good quality webcam has become a must have tool over the…
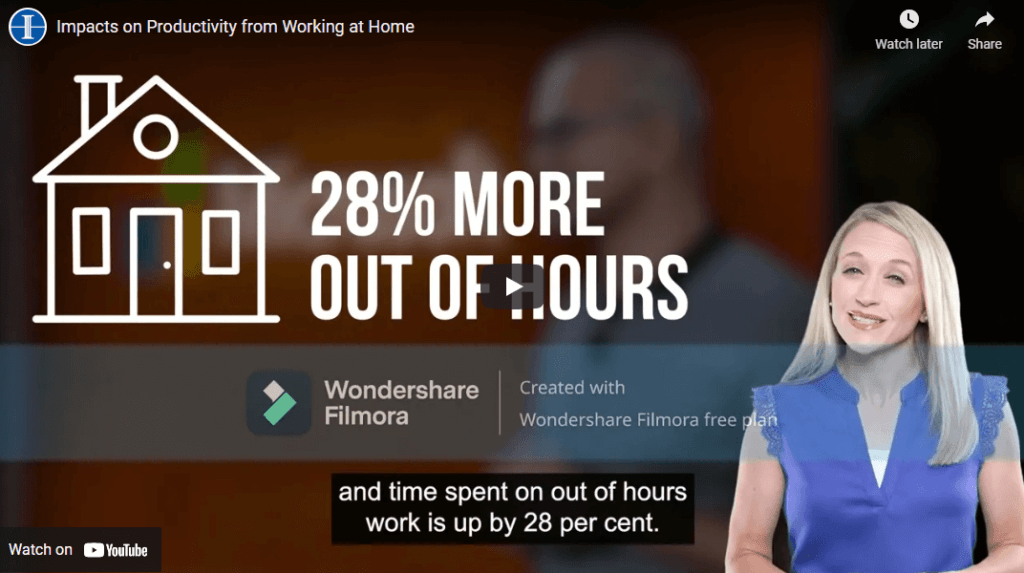
Impacts on Productivity from Working at Home
With the new hybrid style work schedule, workers are able to have…
Learn More about New Features to Google
Recently Google has been working about some new features that will help…
What Your Business Should Know About Cybersecurity and Working Remote
With many employees working remote or from home, there is an increased…
Microsoft Tech Update
Microsoft is in the process of re-developing AI facial recognition. Learn more…
How Working from Home Impacts Your Business
With many people working from home, there is a lot of changes…